Stay protected and productive with the Zero Trust approach to cybersecurity
In a world where we work at any time, from any location and on a wide range of devices, companies are discovering the limitations of traditional security models.
Perimeter-based security, VPN’s and verified workstations are no longer enough to handle an increasingly aggressive threat landscape and modern ways of working.
This is especially true for highly regulated verticals like life sciences, finance, energy and public sector.
We need a different approach to cybersecurity, which is more flexible, easier to automate and where communication and data access can be easily verified and controlled.
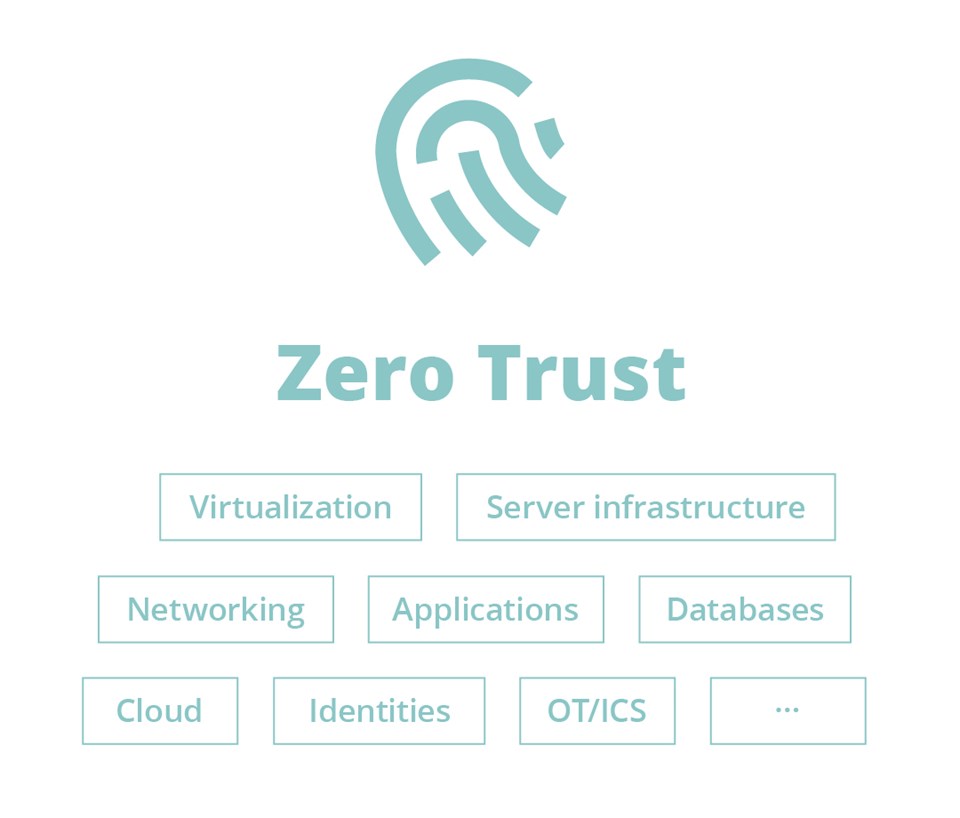
We need Zero Trust.